These insights are then used to inform critical business decisions. A firm grasp of business strategy and KPIs.
 Business Intelligence Bi Analyst Resume Sample 2021
Business Intelligence Bi Analyst Resume Sample 2021
Excellent leadership and interpersonal skills.

Business intelligence analyst skills. Instant industry overview Market sizing forecast key players trends. The ability to write SQL. What makes a good BI analyst.
It can include anything from data mining to prescient demonstrating to the prescriptive investigation. As organizations build up their business intelligence capabilities by drawing on querying data mining data visualization and other data analytics technologies BI analysts are tasked with using those tools to produce insights that can inform and guide business decision-making. Organization and Time Management Skills Time management skills are among the best business intelligence analyst skills too.
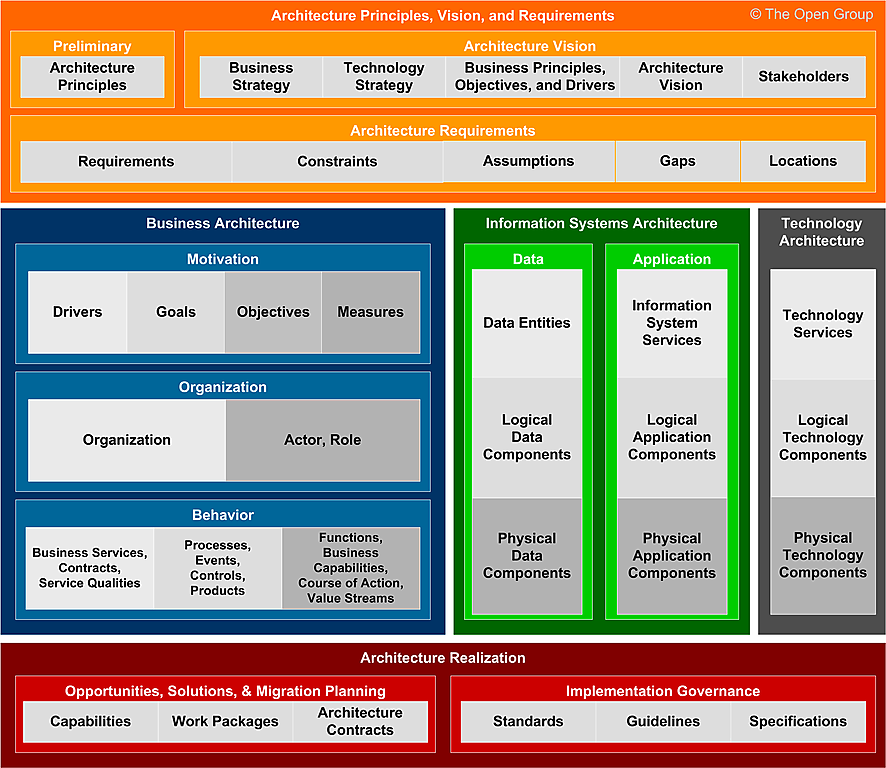
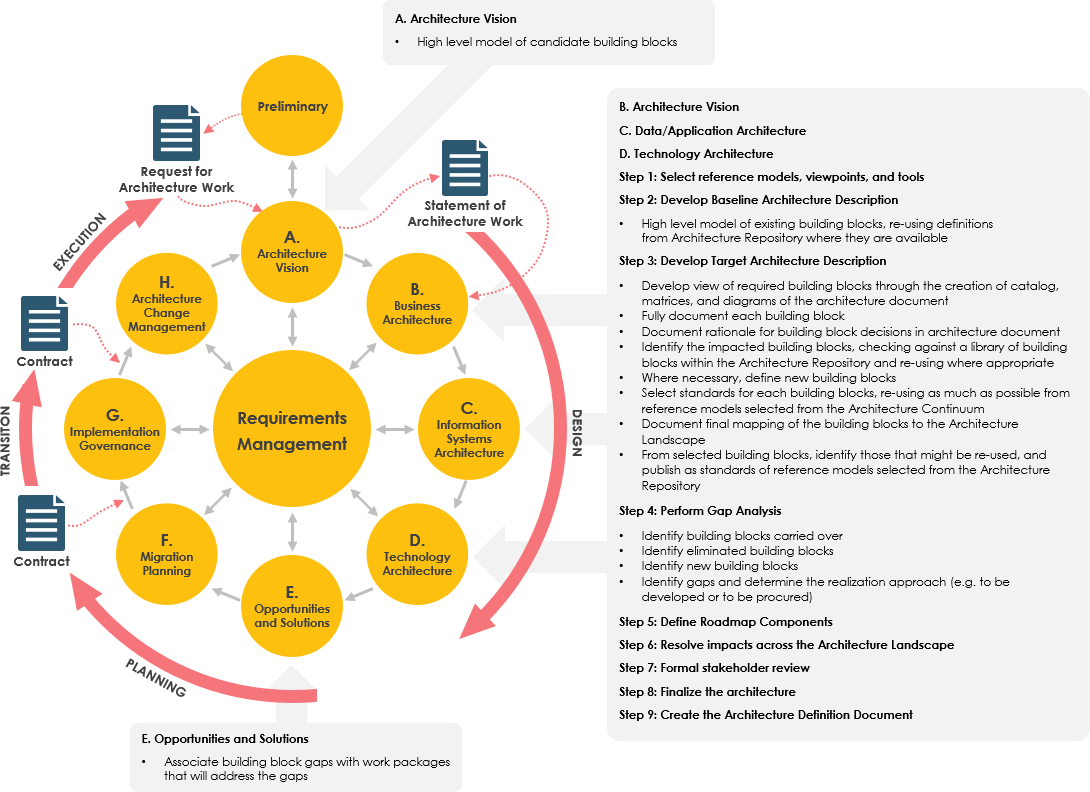
Business intelligence analysts must have a range of skills in big data especially data analysis as well as keen business understanding. With the data collected they help develop a picture of companys competitivness compared to other player in the market. However data architects data analysts and business intelligence analysts all need strong BI skills as well.
Ad Download Business Intelligence Market Reports from 10000 trusted sources. Analysis skills In business intelligence analytics the investigation is a subset including measurements expectation and enhancement a way to business information disclosure. Instant industry overview Market sizing forecast key players trends.
What is a Business Intelligence Analyst. What Are Business Intelligence Skills. Business Intelligence Analysts are usually responsible for gathering business data through many different ways including gather this data through mining a companys computer data looking at competitor data and industry trends.
Lets take a look at relevant business intelligence analyst skills. Business intelligence is a technology-driven process so people who work in BI need a number of hard skills such as computer programming and database familiarity. Business analytics professionals mix of technical and non-technical skills makes them uniquely qualified to provide businesses with the competitive edge so badly needed in a big data world.
Ad Download Business Intelligence Market Reports from 10000 trusted sources. Good knowledge and ability to work with specific software is among the most valuable business intelligence analyst skills. A fundamental understanding of SQL and the technical aspects of BI.
Like it or not the more technical you are the more valuable you are as a business intelligence analyst. Assuming you already have an excellent understanding of the business youre analyzing a prerequisite here are some very useful skills to have. Business intelligence analyst skills To become a successful BI analyst youll need a mix of technical soft and analytical skills.
A Business Intelligence Analyst is responsible for taking the data that a company holds and mining it to achieve valuable insights. The job requires you to mine data using complex tools and. The insights play a crucial role in shaping the companys future and the way it operates.
Relevant and demonstrable experience in the BI analyst field.